Network and cybersecurity professionals often encounter entries like 203.160.175.158.14001 in threat logs, firewall reports, or SIEM alerts. This format combines a specific IP address, 203.160.175.158, with port 14001, pointing to potential inbound or outbound traffic. For SOC analysts, IDS/IPS engineers, firewall specialists, and penetration testers, understanding these tuples is key to spotting normal activity versus risks. IT administrators and system engineers may also see them in server logs. This guide breaks down the details simply, with actionable steps to help you analyze and respond effectively.
IP addresses serve as unique identifiers for devices online, much like a street address for mail delivery. Ports act as specific entry points, directing traffic to the right application or service. When combined as 203.160.175.158.14001, it specifies a connection attempt to that IP on that port. In cybersecurity threat logs, these appear during connection tracking. High-numbered ports like 14001 are often used for custom or private services, not standard ones like web traffic on port 80.
IP and Port Basics Explained
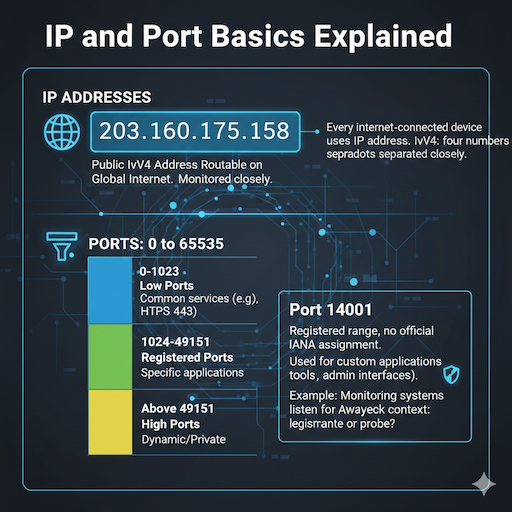
Every internet-connected device uses an IP address. The type here is IPv4, with four numbers separated by dots. IP address 203.160.175.158 is public, meaning it’s routable on the global internet. Public IPs face more exposure, so network monitoring IP tools watch them closely.
Ports range from 0 to 65535:
- Low ports (0-1023): Reserved for common services (e.g., HTTPS on 443).
- Registered ports (1024-49151): For specific applications.
- High ports (above 49151): Often dynamic or private.
Port 14001 falls in the registered range but has no official IANA assignment for a standard service. It can be used for custom applications, such as internal tools or admin interfaces. For example, some monitoring systems listen on this port for updates. In TCP/UDP port identification, always check context – it could be legitimate traffic or a probe.
Background on the IP Address
Data from reliable sources shows IP address 203.160.175.158 belongs to the PTTNET IP block, owned by the Philippine Telegraph and Telephone Corporation (PTT). This is a legitimate Philippine ISP IP operating under the AS18233 network.
Key details:
- Location: Makati City, Philippines (with ties to the Manila area).
- Geolocation: IP geolocation Philippines tools pinpoint it in the Asia-Pacific region.
- Block: Part of 203.160.175.0/24, a subnet with 256 addresses.
- Abuse contact: abuse@ptt.com.ph for reporting issues.
No hosted domains or major services are tied directly to this IP. It’s typical for ISP-assigned addresses, which support residential or business users. Reputation checks show no significant abuse reports – it’s generally neutral.
For range info, see DB-IP IP Range Details. For ASN and block specifics, check IPinfo AS18233 Block.
Why This Combo Appears in Logs
In security log IP reviews, 203.160.175.158.14001 might show as a source or destination. Reasons include:
- Legitimate connections from Philippine users.
- Automated scans probing open ports.
- Custom apps using high ports.
No evidence links this specific pair to widespread threats. Searches for abuse or malicious activity yield no reports. However, any unusual public IP address scanning should trigger a review.
Network intrusion attempt detection relies on patterns: sudden spikes, failed logins, or odd protocols.
Practical Steps for Analysis and Monitoring
Follow these steps to investigate 203.160.175.158.14001 in your environment.
How to check IP 203.160.175.158 in network logs:
- Log in to your SIEM (e.g., Splunk, ELK).
- Query for the IP: src_ip = “203.160.175.158” OR dest_ip = “203.160.175.158”.
- Add port filter: port = 14001.
- Review timestamps and volume.
Identify suspicious activity on port 14001:
- Look for repeated SYN packets (scan signs).
- Check the payload if captured.
- Correlate with other alerts.
Steps to trace port 14001 activity in firewall logs:
- Access firewall interface (e.g., Palo Alto, Cisco).
- Filter logs by port 14001.
- Note associated IPs and actions (allow/deny).
- Export for deeper analysis.
Best practices for logging IP 203.160.175.158 connections:
- Enable detailed logging on edge devices.
- Use centralized collection.
- Set retention for at least 90 days.
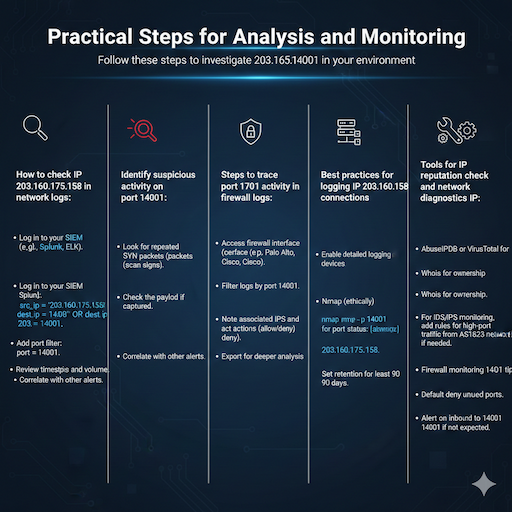
Tools for IP reputation check and network diagnostics IP:
- AbuseIPDB or VirusTotal for reports.
- Whois for ownership.
- Nmap (ethically) for port status: nmap -p 14001 203.160.175.158.
For IDS/IPS monitoring, add rules for high-port traffic from AS18233 network IPs if needed.
Firewall monitoring 14001 tips:
- Default deny unused ports.
- Alert on inbound to 14001 if not expected.
Port scanning detection:
- Use tools like Snort or Suricata.
- Block repeat offenders.
In the Philippine ISP PTTNET IP block analysis, the range supports standard internet services. Monitor the full 203.160.175.0/24 network with tools like Zabbix for anomalies.
Network security monitoring for AS18233 IPs involves watching routing and peers. No major issues noted.
Detect intrusion attempts from IP 203.160.175.158 by baselining traffic.
Security analysis of public IP addresses in the Philippines shows varied reps, but this one appears clean.
Monitoring tools for the IP 203.160.175.0/24 network include PRTG or Nagios.
Investigating network threats using IP and port logs starts with correlation.
Real-World Examples and Tips
SOC analysts might see this in SIEM alert IP during global scans. One common case: automated tools probing high ports for vulnerabilities.
Pen testers use similar pairs in recon phases.

Tip: In network security analysis, combining geo data – traffic from the Philippines on non-standard ports warrants a context check.
For IT admins: Review access logs for unexpected outbound to this pair.
Stats show port scans remain common, with high ports targeted for custom exploits.
FAQs
What is 203.160.175.158:14001?
This is a special internet address with a number called a port. The address is 203.160.175.158, and the port is 14001. It comes from a company in the Philippines that helps people go online. It is just a way for computers to talk to each other!
Is it a threat?
No, it is not known to be bad or scary right now. There are no big stories saying it is a hacker or a virus. But if you see it on your computer a lot and do not know why, tell a grown-up to check it and keep you safe1.
How to block it?
You can stop it from connecting to your computer very easily. Go to your computer’s settings and make a rule in the firewall that says “no” to this address or port. It is like putting up a wall so nothing bad can come in!
Why port 14001?
Port 14001 is not a regular number like ones for websites or emails. Someone probably picked it just for their own special app or game. Lots of people use big numbers like this for their own fun or work stuff online2.
Conclusion
203.160.175.158.14001 refers to a standard public IP from PTT in the Philippines, paired with a non-standard port often for private apps. For network pros, it’s a routine log entry worth checking via IP reputation check, log queries, and monitoring best practices. No red flags stand out, but vigilance keeps systems secure.
Have you encountered 203.160.175.158.14001 or similar high-port traffic from Asian ISPs in your logs? What steps did you take3?
References
- IPinfo for AS18233 Block – ASN, company, and subnet information. ↩︎
- DB-IP for IP Range Details – Ownership and location data for the 203.160.175 range. ↩︎
- General Guide on IP-Port Combos – Overview of ↩︎




